Chapter 4:
Don’t Sell Compliance —
Sell Risk Assessment & Management
Chapter 4 illustrates how to change the conversation around compliance with your clients. Rather than selling compliance, showcase how compliance can streamline their risk assessment and risk management processes.
Shifting the Narrative
Many small businesses view compliance as something they must maintain to operate, but few of them truly understand its value. Some ignore compliance management entirely. Others simply check off the box and move on to the next item on their to-do list without giving it another thought.
As an MSP, it’s your responsibility to shift the narrative. Compliance isn’t just about getting a check mark that lets your clients operate legally based on some government or industry regulations — it’s about proving they can protect sensitive data and proactively assess and manage risk.
Achieving compliance isn’t a one-time thing or a one-off task — it’s not something they can do today and never think about again. To scale successfully and reduce risk over the long term, your clients must maintain compliance by building it into their risk management process using compliance management software. But they need your help.
So, how do you change the conversation?
Focus on continuous improvement.
Don’t position compliance as a one-and-done effort — position it as an ongoing process. Ongoing risk management is significantly more effective at preventing threats and shoring up vulnerabilities than one-time compliance checks. Help your client build out a scalable, sustainable risk management process now so they don’t have to stress about potential consequences in the future (or worse, find themselves unprepared when an incident occurs).
Highlight the need for operational resilience.
Compliance monitoring tools help you establish a baseline for security practices. The goal is to identify gaps and vulnerabilities and then adopt best practices to protect against likely threats. This approach lets you focus on monitoring threats and vulnerabilities (and preventing them altogether!) rather than scrambling when incidents occur. By building out an incident response protocol, you can help clients proactively mitigate the impact of cyberattacks.
Think about the long-term.
Ongoing risk management provides deeper insight into organizational vulnerabilities. Once you establish a baseline, your clients can adopt new technologies with risk management built into the process, allowing them to confidently scale. If you can help them align risk management practices with long-term business objectives, they will be better positioned for future growth.
Make it easy for them to adopt.
The best thing you can do to help your clients adopt risk assessment and management is to make it easy. You can do this by bolting on compliance and risk management solutions to your existing offerings. Be sure to tailor your compliance automation solutions to each client’s needs (based on industry, region, offerings, etc.). If you can prove your expertise in the space, gain credibility in the market, and take risk management out of their hands, your clients can focus their energy on what they do best.
Key Components of Risk Assessment and Management
Follow this 9-step roadmap to roll out risk assessment for your clients.
Asset Audit:
Threat Identification:
Risk Analysis:
Risk Prioritization:
Risk Mitigation:
Ongoing Monitoring:
Incident Response Protocol:
Training and Awareness:
Client Communication:
Risk Assessment Matrix
Use this Risk Assessment Matrix to identify and prioritize risks based on their likelihood of occurring and their level of impact on the business
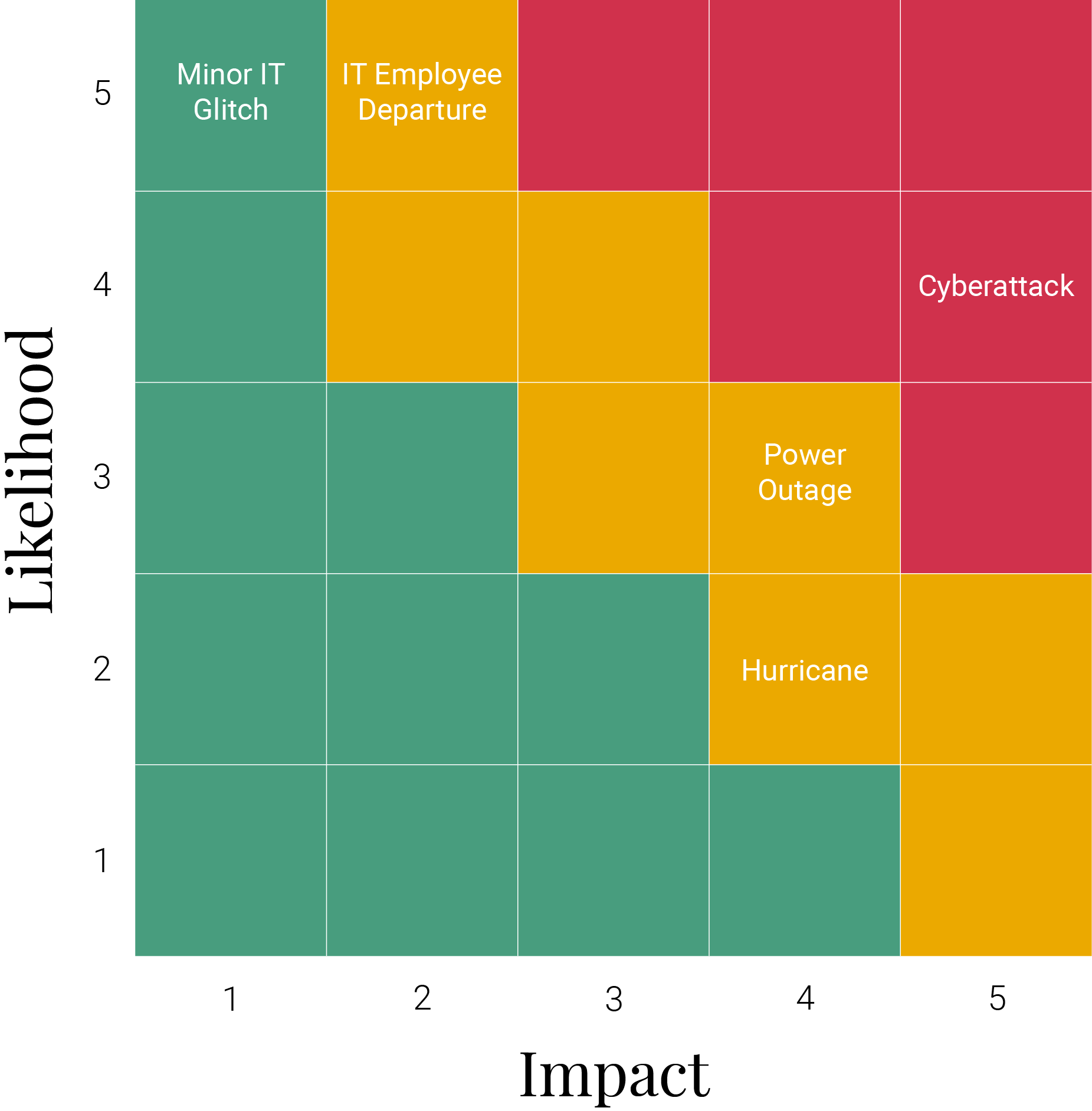
Risk Analysis Matrix Template
| Risk ID | Likelihood (1-5) | Impact (1-5) | Risk Score (Likelihood x Impact) | Risk Score (Likelihood x Impact) | Responsible Party | Status |
|---|---|---|---|---|---|---|
| Cyberattack | 4 | 5 | 20 | Implement strong cybersecurity measures, backups, regular training, and incident response plans. | IT Manager | Active |
| Hurricane | 2 | 4 | 8 | Develop a disaster recovery plan and business continuity plan. | Operations Manager | Active |
| Power Outage | 3 | 4 | 12 | Install backup generators and create an emergency response plan. | Facilities Manager | Monitored |
| IT Employee Departure | 5 | 2 | 10 | Develop knowledge transfer programs and cross-training initiatives. | HR Manager | Under Review |
| Minor IT Glitch | 5 | 1 | 5 | Maintain regular software updates and support resources. | IT Support | Monitored |
Columns:
- Risk ID: A unique identifier for each risk.
- Likelihood (1-5): The probability of the risk occurring (1 = very unlikely, 5 = very likely).
- Impact (1-5): The potential impact of the risk on the business (1 = low impact, 5 = high impact).
- Risk Score: The overall risk score calculated by multiplying likelihood x impact.
- Mitigation Strategies: Actions or plans to reduce the likelihood or impact of the risk.
- Responsible Party: The person or team responsible for managing the risk.
- Status: Current status of the risk (e.g., "Under Review," "Mitigated," “Monitored,” "Active").
How to Use the Template:
- List all potential business risks in the first column (we’ve included five examples to get you started).
- Assess and score the likelihood and impact for each risk.
- Calculate the risk score and prioritize risk management starting with the highest risk level.
- Develop and note mitigation strategies.
- Assign responsibility and track the status.
Feel free to customize this template according to your specific needs!
Benefits of a Proactive Approach to Cybersecurity
Early Threat Detection:
Reduced Downtime:
Cost Savings:
Scalability and Flexibility:
Now that you have the “why” covered, let’s move on to the “how.”
Learn how to package your CaaS offering in Chapter 5.

Chapter 3
Client Assessment
