Automatically collect and continuously update compliance evidence to keep your clients compliant through integration of ControlMap and ThreatMate.

ThreatMate is an advanced attack surface management tool designed to monitor and secure networks from various cybersecurity threats. This comprehensive platform scans both external and internal network environments, including behind the firewall, and extends its monitoring capabilities to cloud services like Microsoft O365 and Google Workspace. By leveraging artificial intelligence (AI) and machine learning (ML), ThreatMate identifies security exposures and creates targeted mission plans for vulnerability remediation, ensuring a secure cyber environment across all connected devices and endpoints.
MSPs that use ThreatMate achieve the following benefits:
Integrating ControlMap and ThreatMate allows for automatic collection of scan results by company and mapping to frameworks. It can be configured to run a scan and update the results weekly for continuous checks and updates.
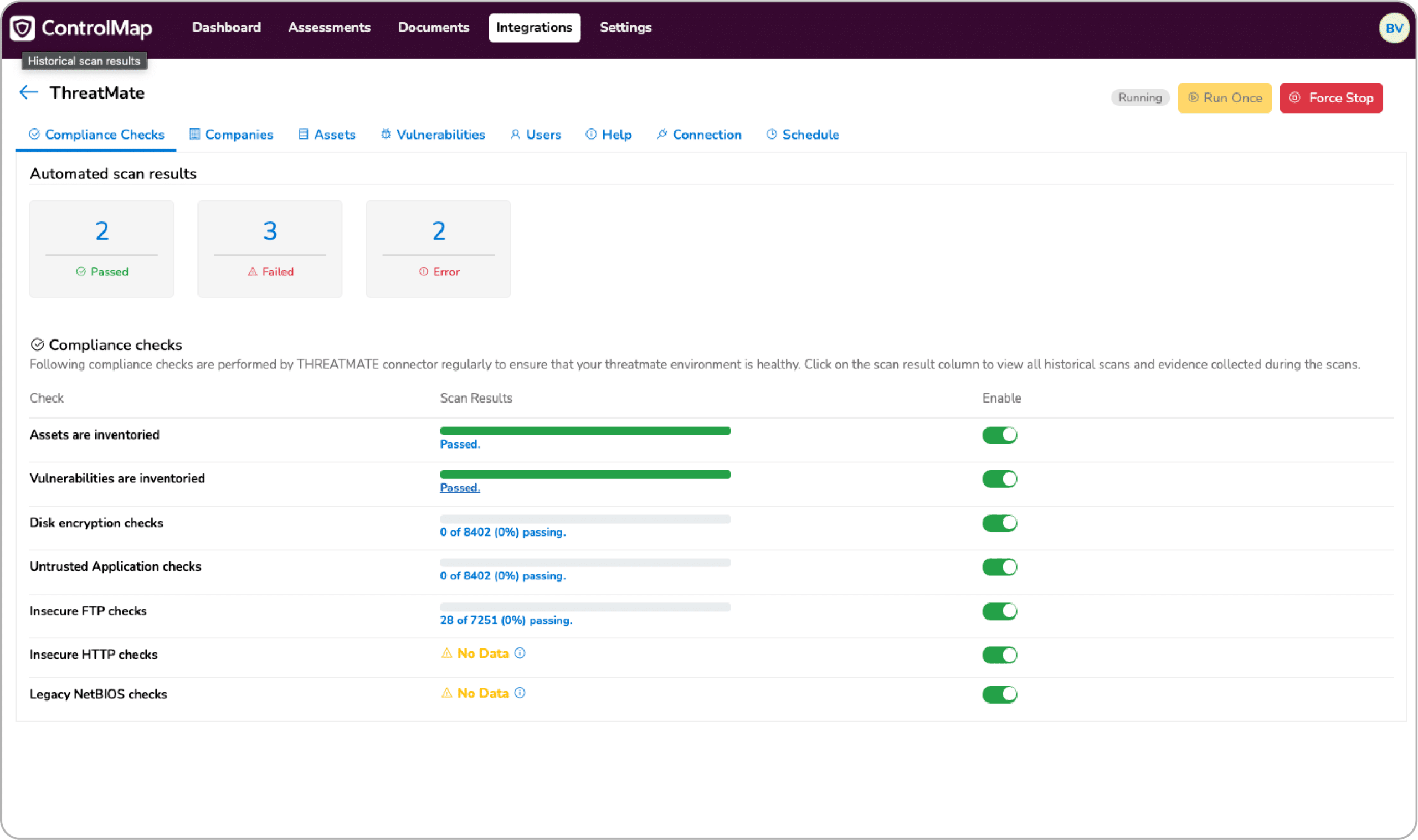
Collection of evidence - Once you’ve connected ThreatMate to ControlMap, the connection automatically starts collecting compliance check results, companies, assets, vulnerabilities, and user data from ThreatMate scans on a regular schedule.
Mapping to frameworks - The collected evidence is then mapped to over 50 security and compliance frameworks, such as SOC 2, ISO 27001, HIPAA, FTC Safeguards, CIS Controls, CMMC, and other frameworks and security standards. Mapping the evidence automatically provides a detailed view of any gaps that need to be addressed.
Ongoing automatic updates - The ControlMap-ThreatMate integration is not simply a one-time check. ControlMap can be configured to regularly sync with ThreatMate to provide up-to-date evidence & vulnerabilities. This will update the evidence based on the current settings, ensuring that your team is aware of any configuration changes, new risks or gaps so you can take remedial action to maintain compliance.
Connecting ControlMap and ThreatMate reduces hours of manual data imports and regular reviews. It automatically retrieves, updates, and stores current evidence required for compliance frameworks so your team can focus on maintaining and improving security.
ControlMap connects with and retrieves the following data from ThreatMate:
Compliance checks - These checks are regularly run to ensure the ThreatMate environment is healthy
Companies - A list of companies in ThreatMate
Assets - A list of assets as well as scan results
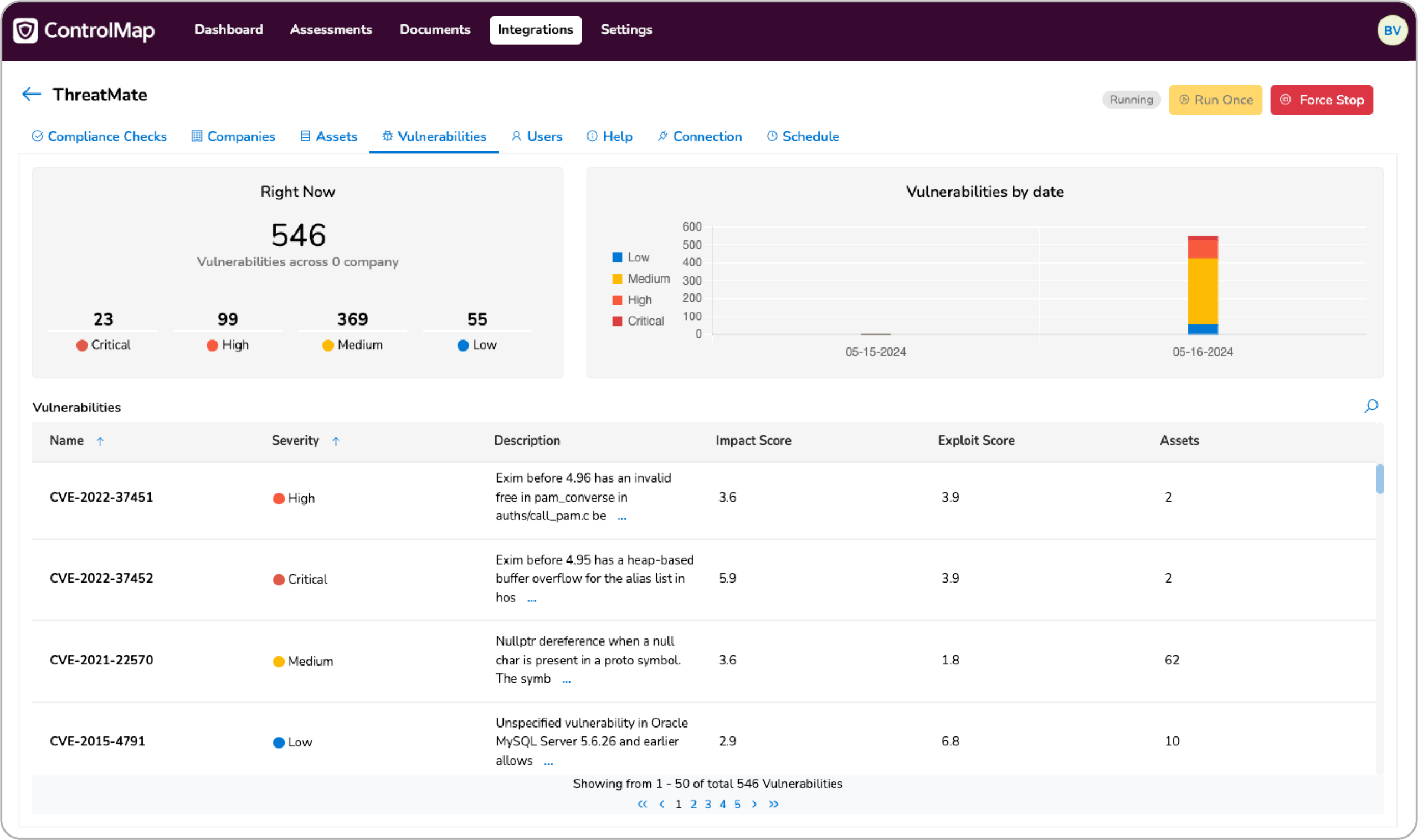
Vulnerabilities - A list of vulnerabilities classified into Critical, High, Medium, or Low status as well as descriptions
Users - A list of uses including their training status
From the ControlMap dashboard, click integrations > add integration > ThreatMate. Enter your credentials (username and password), and click connect. More details can be found in our help center.